Tackling Burp and Android
How to get Burp Suite to intercept traffic from an Android Emulator. Even on Macbooks with M1 chips.

You know the drill...Go read my Disclaimer...
Ramblings
So you're an ethical hacker/pentester trying to test a mobile application and need a working proxy to intercept some communication right? Burp or Zap doesn't work anymore since the 1980s right because of good ole SSL Pinning and such? We know that using a rooted device would help us in bypassing the security features, but how long would it take set that up? Worse if you're an M1 User...NOTHING SEEMS TO WORK RIGHT? JK...Pick up your Browser and Google.
Well...this is what we're gonna go through today. Let's actually do some work in a smarter fashion.
So...What do I need?
1) A Sensible Computer running Linux, OSX...okay...Windows is fine too...
2) A Proxy of Your choice (Burp/ZAP/Charles) ...We finna use Burp tho...
3) Android Studio and other SDK Packages
4) RoodAVD via Github (Big Ups to NewBit @xda-developers)
5) MagiskTrustUserCerts via Github as well
This works on Linux, macOS and Windows but I will be working from macOS (M1)...Difficulty MAXED...
Okay...so I hope you have Android Studio and other SDK Packages including adb and emulator tools installed for command line. I won't be writing a tutorial on that...but here
- How to install Android Studio
- How to install Burp Suite
- How to add android sdk tools to PATH

Tutorial Time?
Lets clone rootAVD and head to the folder.
git clone https://github.com/newbit1/rootAVD.git
cd rootAVD
Make sure your AVD is running and given you have a similar folder structure, run...
./rootAVD.sh ~/Library/Android/sdk/system-images/android-31/google_apis_playstore/x86_64/ramdisk.img
Your AVD Should restart automatically here, but if it does do a cold boot.
Just note that the 'android-31' section can be changed to whatever version you have installed once compatitble.
Go ahead and open Magisk as seen below.

Once thats open, its gonna require ANOTHER REBOOT! 😃 So just get that done...
Lets use Root Checker to verify root access...
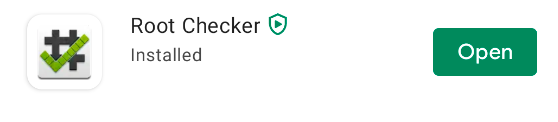
Once you click Verify Root
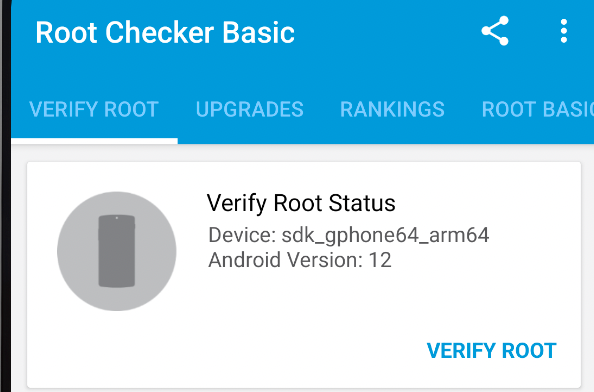
We should be able to get this...thus verifying ROOT!

NOW LETS CONNECT BURP!
So this process entails having to install a cert from BURP. Lets create a new listener in burp first.
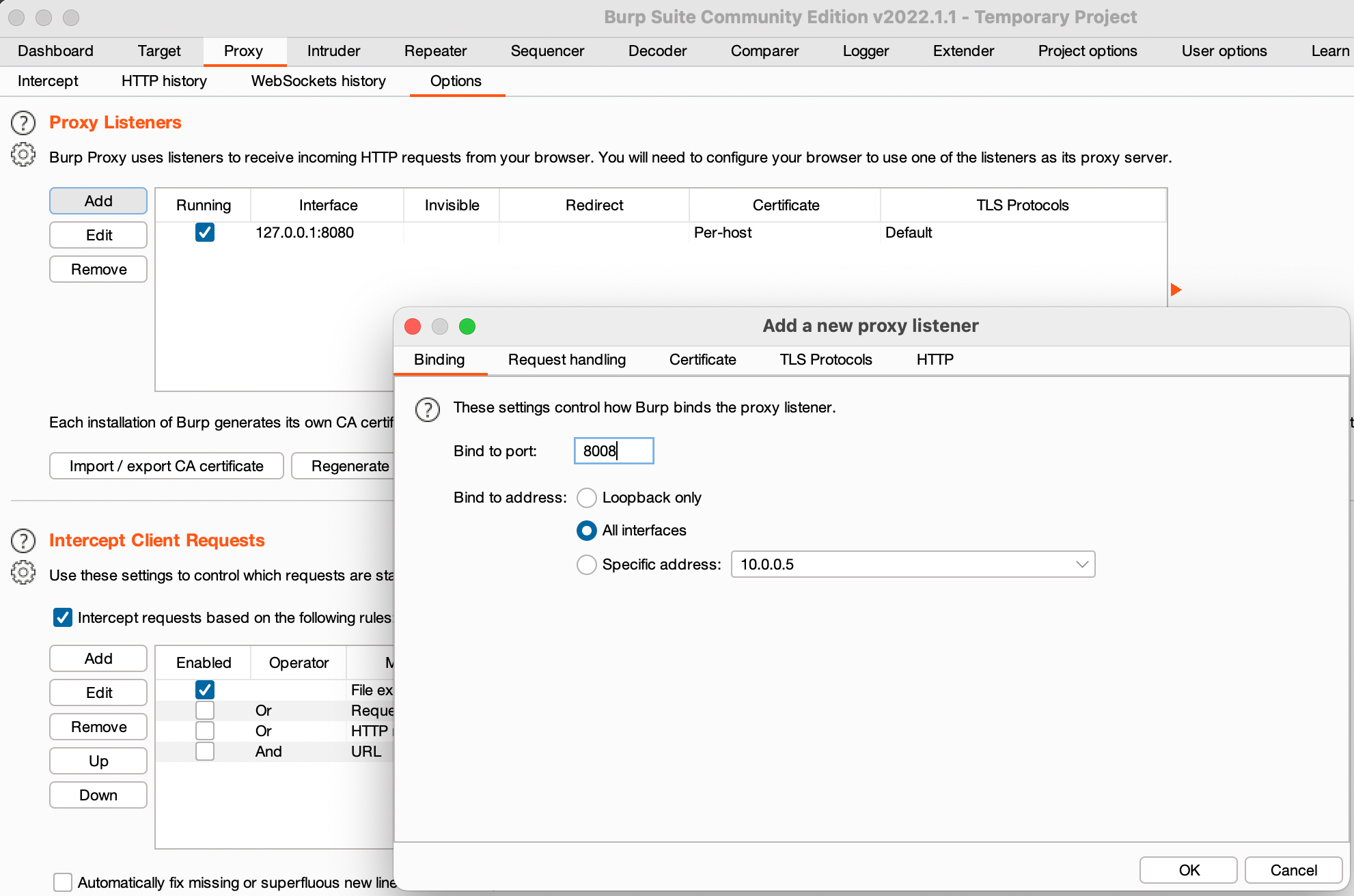
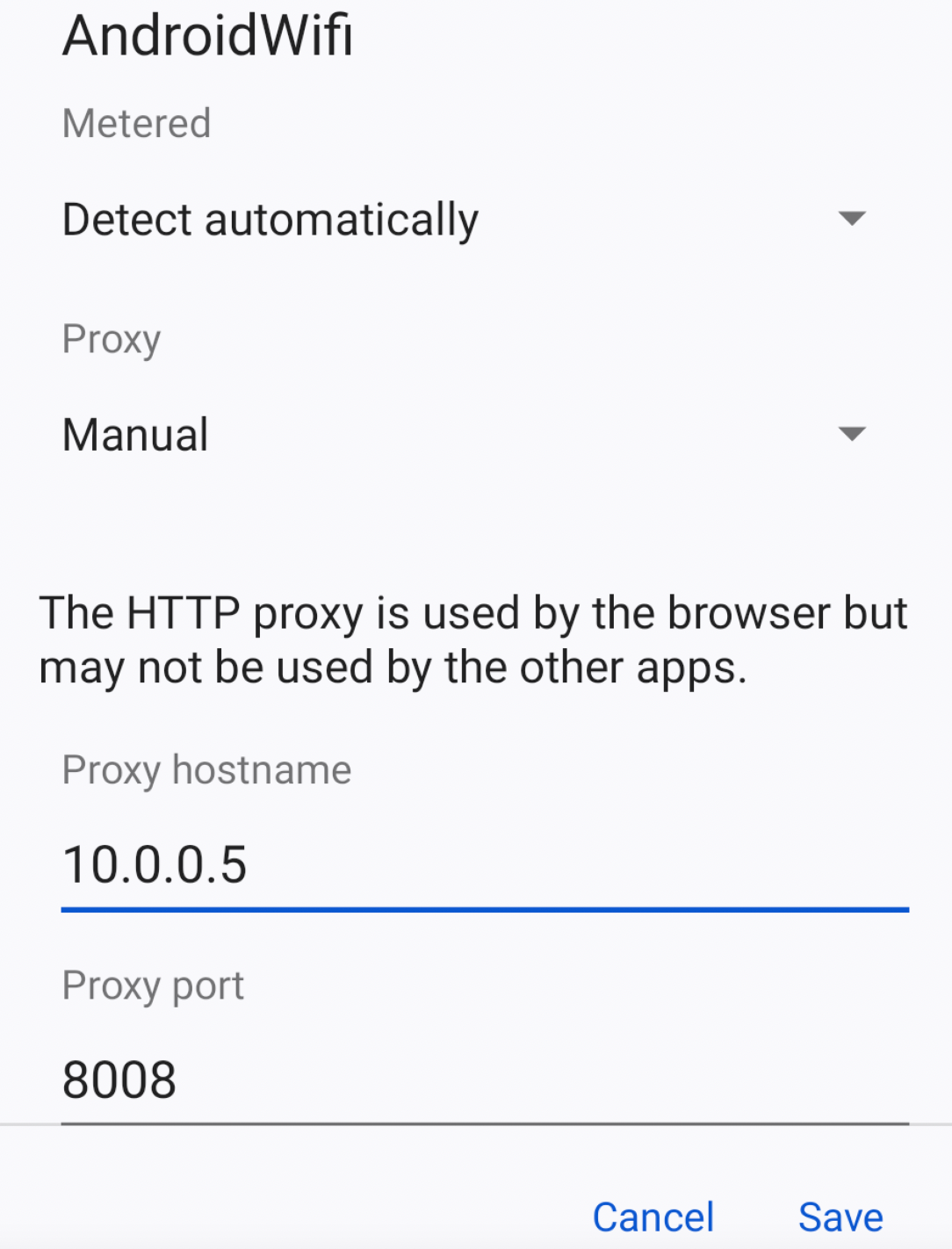
We're gonna connect our AVD to that Burp Proxy Listener via the WiFi Settings.
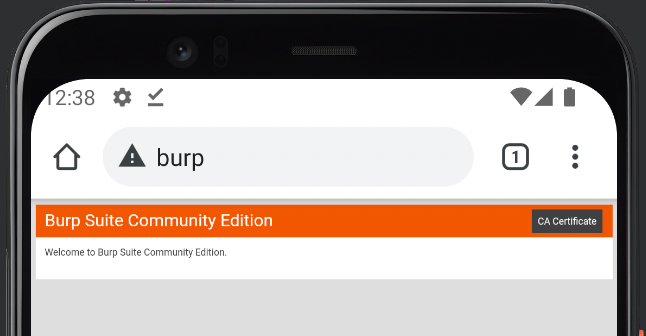
Once thats done, we can browse to "http://burp/" and download our cert from there.
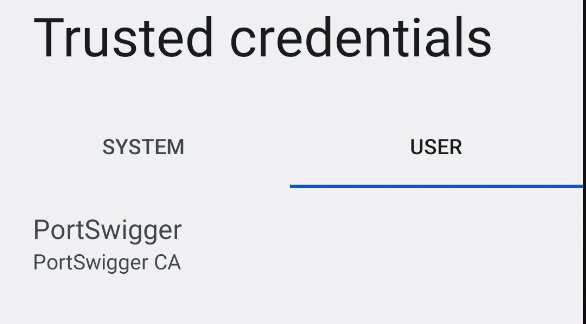
Now lets head to Settings and search for "Install a Certificate". Be sure to select the one under Security > Encryption and Credentials, then Install a Certificate > CA Certificate > Install Anyway and select cacert.der.
You view if it got added in Trusted Credentials under users.
BUT WAIT! THERE'S MORE!
You still can't intercept all traffic with burp as yet! But just bare with me a lil bit more. We're almost there 😂...
We're gonna need MagiskTrustUserCerts from Github. Be sure to add this file to your downloads folder on the AVD so you can access it from there.
So lets head back to Magisk and Select the Modules section, Select from downloads and select the File.
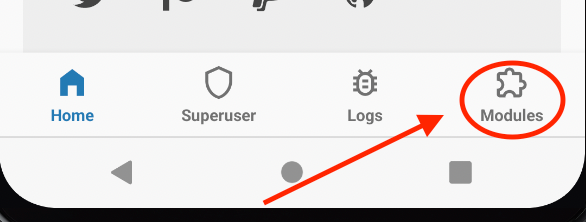
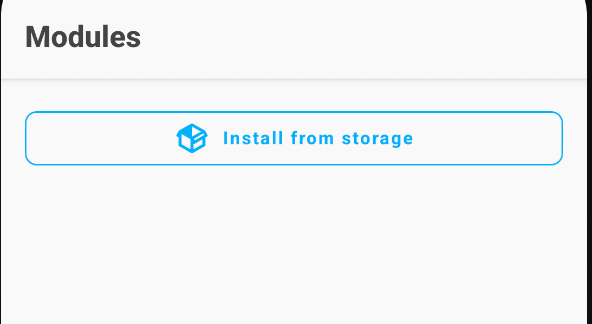
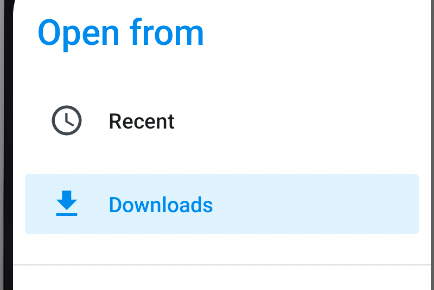
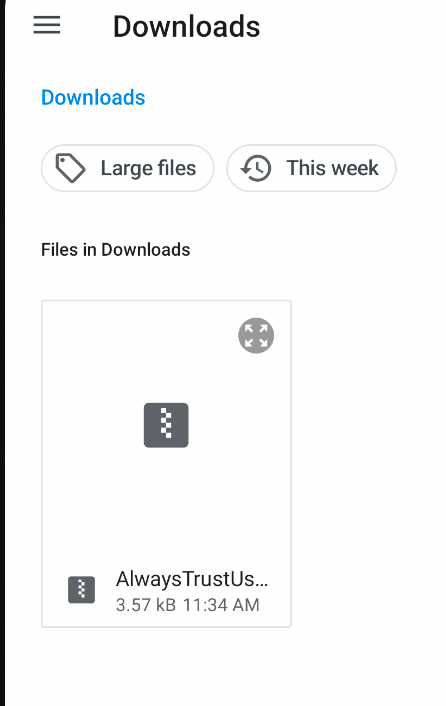
Once the files is selected, You should see this. And yea...Reboot again! Lots of rebooting!
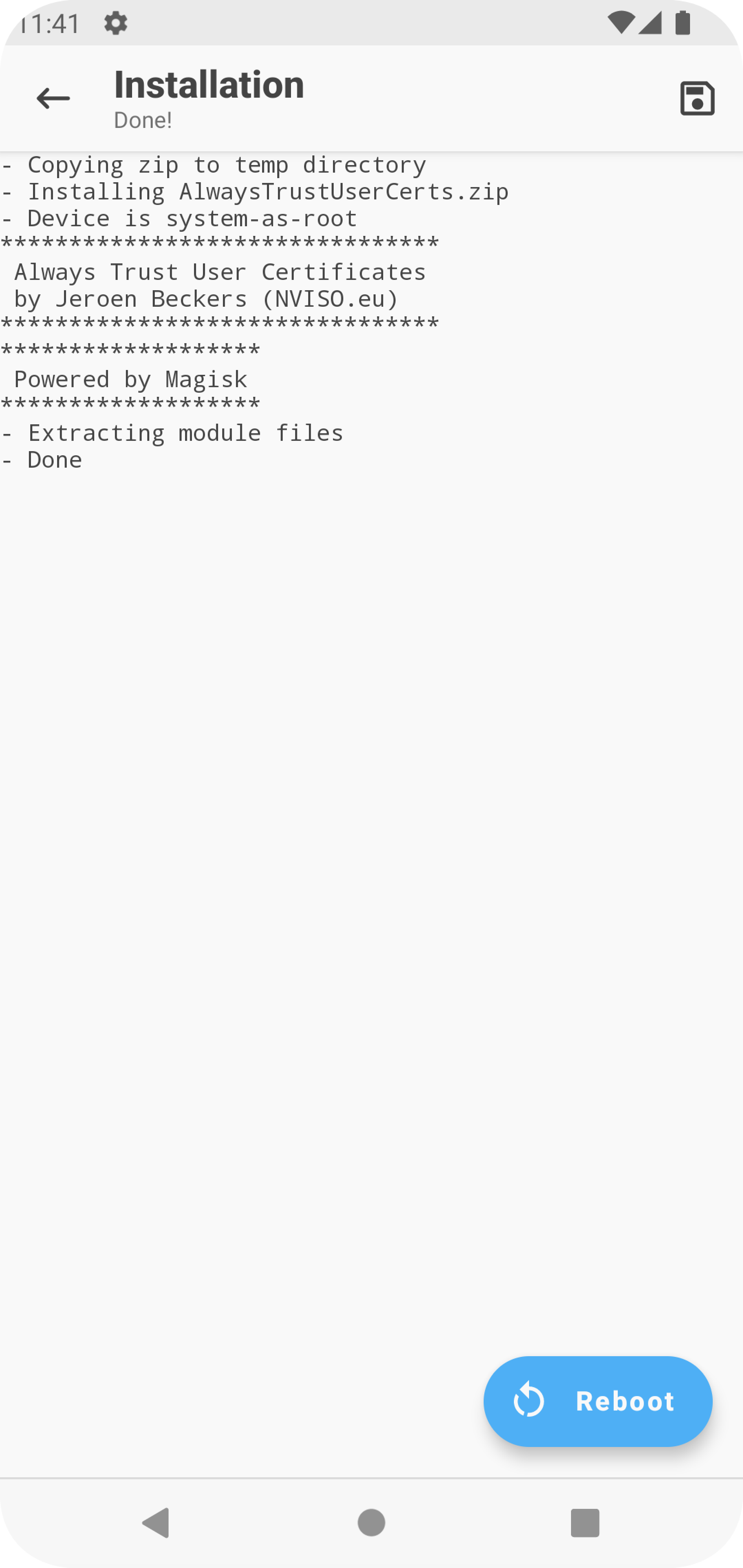
Now you can you can check Burp!
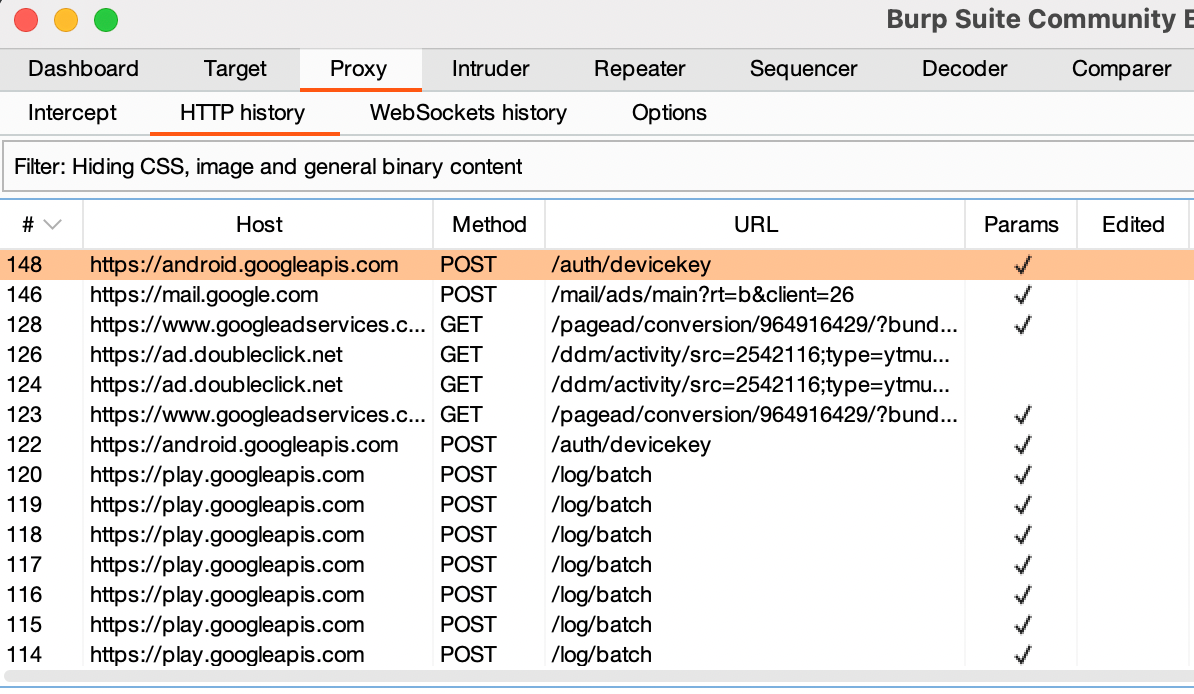

That was kinda long...and annoying...but it works. If you need help or any assistance, please google it. If nothing works, DM me via Twitter. I'll try and google the issue for you as well 😂.